Preemptive Cybersecurity for Critical Operations
Advanced Security Technologies protects governments, global enterprises, and mission-critical infrastructure by preventing cyber attacks before they begin.
Seamless Integration with Your Favorite Security Devices and Tools










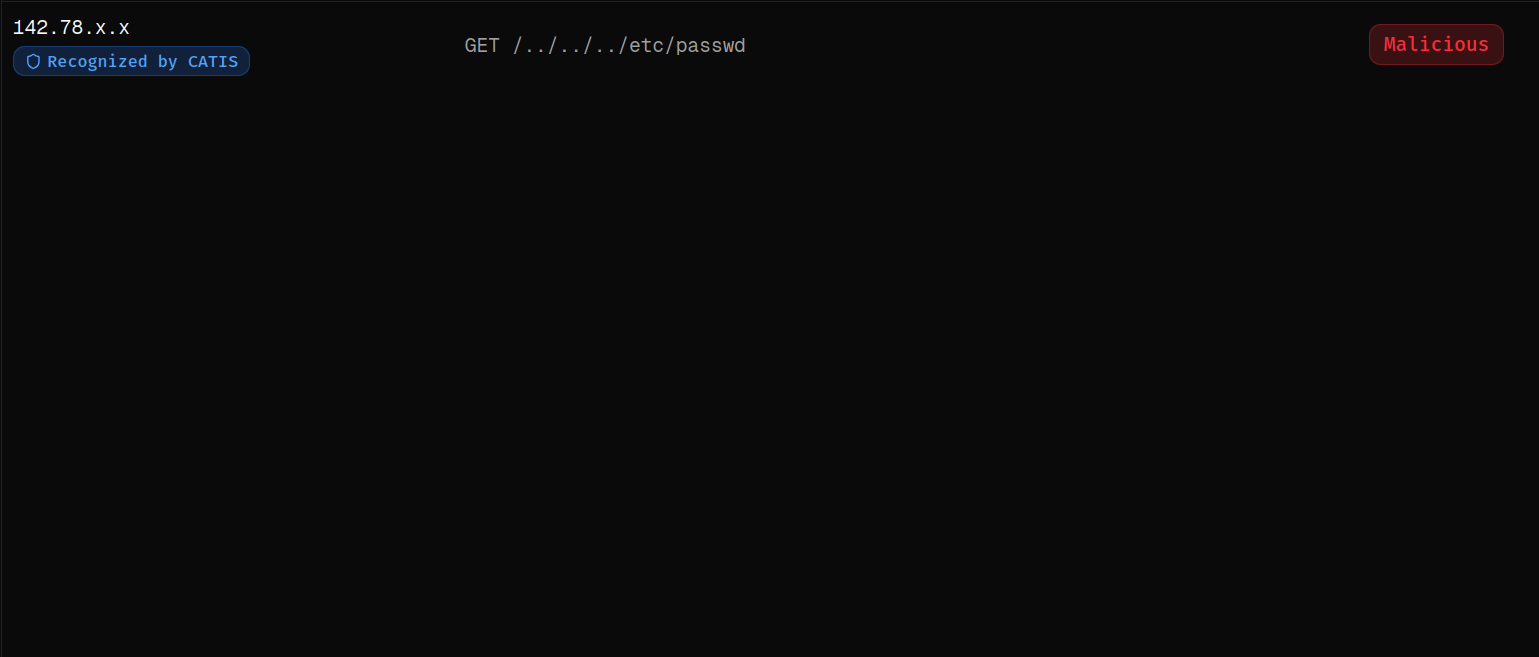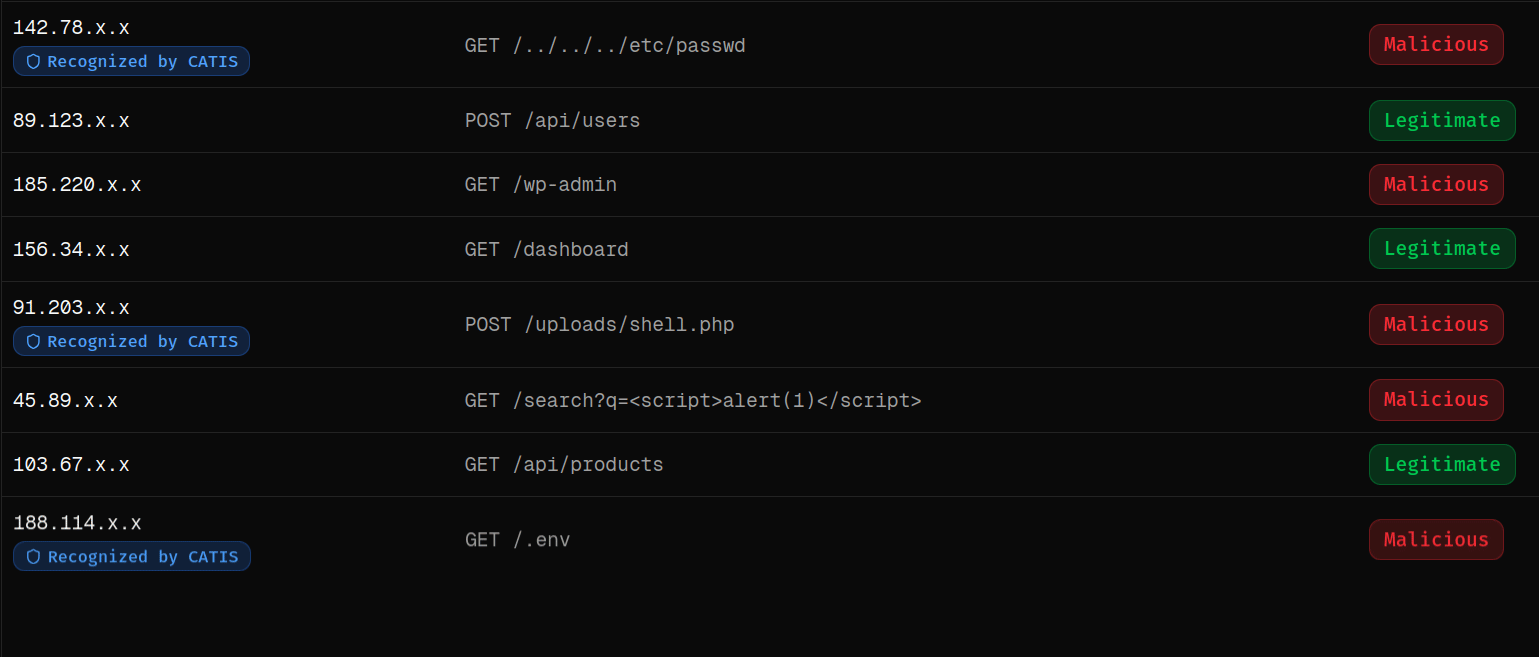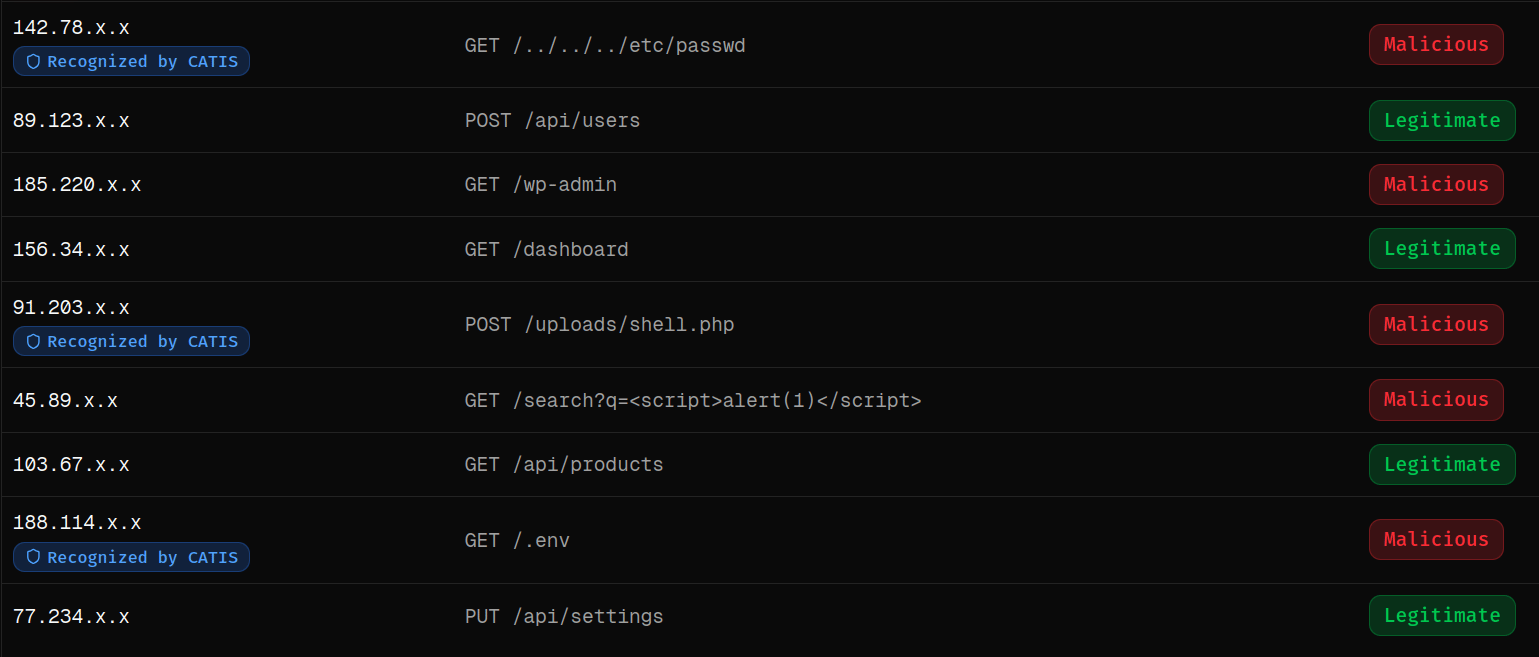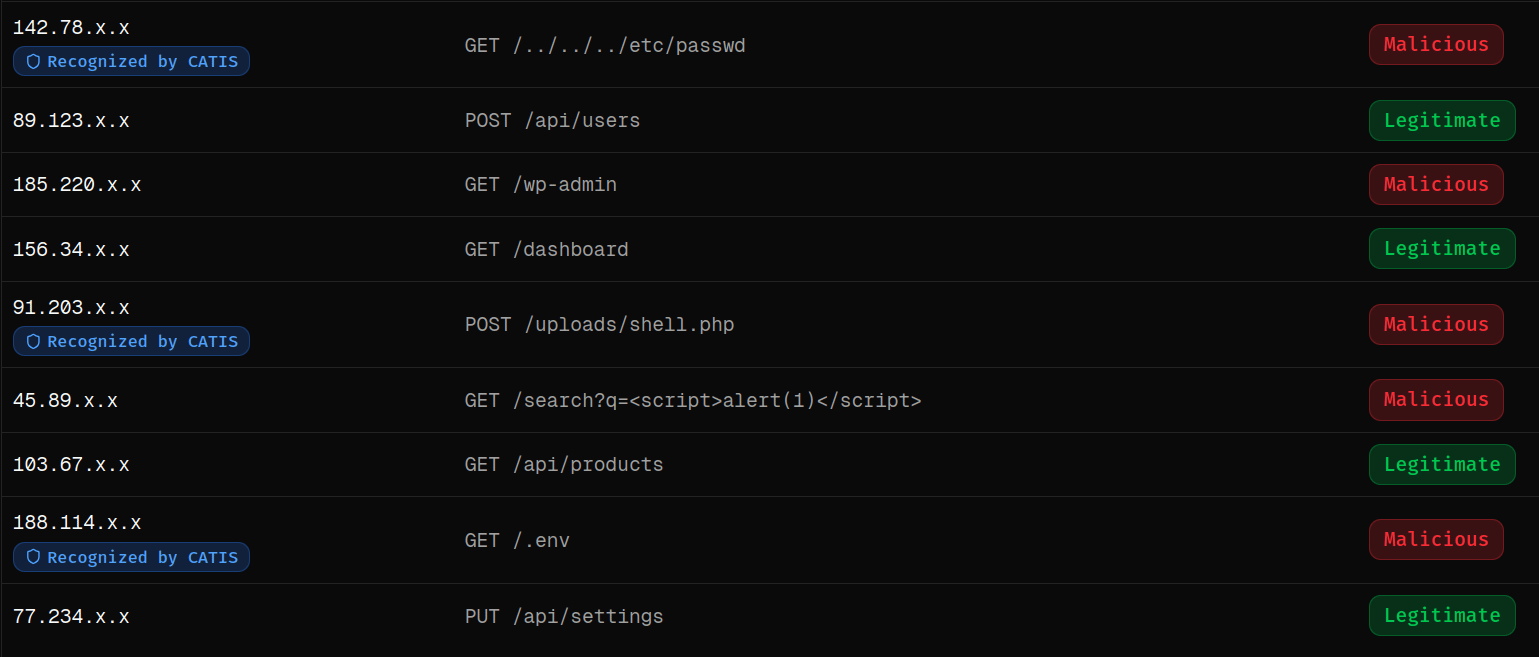
Real-Time Monitoring
Verified Zero-Day Defense
Zero-Day Attacks Detected Before Public Disclosure
Through autonomous deception, cyber-clones, and continuously adapting AI, we observe attacker behavior in real environments – allowing us to prevent zero-day attacks days or weeks before public disclosure.
Log4Shell
We detected Log4Shell exploitation activity on December 9, 2021, the same day it was publicly disclosed, at the very start of global mass exploitation.
Microsoft SharePoint Zero-Day
Our team observed active exploitation on June 5, 2025, over a month before public disclosure on July 20, 2025.
Oracle Zero-Day
AST detected real-world attack activity on October 6, 2025, more than one month before the vulnerability was publicly disclosed on November 10, 2025.
Innovative Cyber Defense
Advanced Cybersecurity Solutions
Innovative, AI-driven security solutions built on patented research and real-world threat intelligence to prevent attacks before they impact critical systems.

Autonomous Defense
NanoFirewall
Self-defending security engine that prevents cyber attacks on devices and networks through adaptive AI, deception, and real-time response.
Adaptive Intelligence
CATIS
Personalized threat intelligence based on real attacker behavior, enabling early detection, deception, and preemptive threat prevention.


Next-Gen SIEM
ASPEN
High-performance SIEM designed for large-scale environments, delivering advanced correlation, compliance, and actionable security insights.
AI-Driven Deception
Baithive
Realistic, self-adapting cyber-clones that lure, analyze, and disarm attackers – collecting unique threat intelligence long before they reach your real infrastructure.

Services
Enterprise-Grade Cybersecurity & Intelligence Services
Defensive, adaptive and preemptive — engineered to safeguard critical infrastructure, corporate systems, and IIoT networks before threats strike.

24×7 Security Operations Center
Real-time monitoring and incident response ensuring continuous protection of your environment.

National Threat Intelligence
Advanced threat intelligence designed to preempt cyber risks targeting critical national infrastructure.

Corporate Threat Intelligence
Tailored intelligence and threat detection aligned with your organization’s specific attack surface.

Managed Security Services (MSSP)
Enterprise-grade security operations and protection delivered as a fully managed service.

Cyber Risk & Insurance Readiness
Risk assessments and security controls aligned with cyber-insurance and compliance requirements.

Machine Learning Security Assessment
Evaluation and hardening of ML systems against manipulation, poisoning, and adversarial attacks.







